Introduction
The other day my friend Juan Rossi reported a vulnerability in the Almundo billing system. Since then, the vulnerability has been fixed by Superfactura , their billing software provider.
Almundo is one of the biggest travel agencies in Argentina . Their site is among the 250 most visited websites in the country.
The vulnerability allowed anyone to download billing information about their clients by creating a pretty simple HTTP GET request. No programming knowledge required.
Basically, if you had bought anything from Almundo, you would have received an email with a link to your bill. Something like this:
http://asatej.superfactura.com.ar/un_comprobante_pdf.php?s=1&f=73455&tc=F13&tf=B
At plain sight, you can see the type of bill (Factura B) and the number of bill (Factura #73455)
By entering this URL, you could see sensitive information about the client and what they had bought:
- Client’s full name
- Client’s CUIL (Tax identification number in Argentina)
- Client’s address
- What they bought. For example: EZEPUJEZE for a flight ticket from Ezeiza (Buenos Aires, Argentina) to Punta Cana (México)
- How much they paid
Here is a sample of one of the public bills that should have been private:
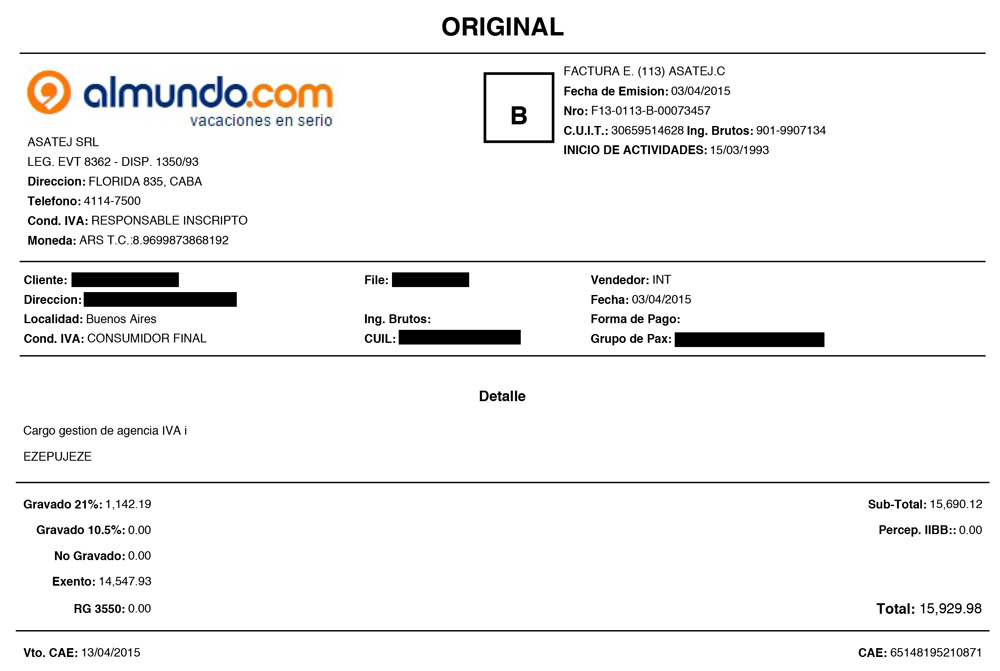
Fortunately, you couldn’t see when this trip was happening.
During the many days that this vulnerability was on production, someone with some programming knowledge could have created a script that iterated from 1 to 100,000 (for the bill number) and from A to C (for the bill type) sending GET requests and downloading all the billing information from Almundo.
Considering that Superfactura has a few clients, we can only assume that this vulnerability was also in production for all of their clients.
At the time of this publication, the company had not released any information about this vulnerability nor if any sensitive data was downloaded by unauthorized users.